Fraud Education
Kemba Credit Union will under no circumstances contact you by phone, text, or email asking you for personal, account, or card information. Unless you have contacted us directly by phone or within online banking, do not give out any personal, account, or card information.
Kemba will NEVER call, text, or email for your personal or account information.
Kemba will NEVER ask you to download anything on your mobile device (except our mobile app), or ask to remote into your device or computer.
Kemba will NEVER call, email, or text asking you to complete test transactions.
If you receive a text, call, or email that appears to be from Kemba Credit Union asking for personal or account information:
- DO NOT click on any links
- DO NOT call any numbers provided
- DO NOT provide any personal or account information (username, passwords, PIN numbers, or security codes)
- Delete the text/email or hang up the phone immediately
Please call Kemba Credit Union directly at 513.762.5070 or 800.825.3622 if you have received any text, call, or email so we can take all appropriate steps to protect your account.
{beginAccordion}
Fraudulent Text Attempts
Kemba Credit Union is aware of fraudulent attempts to obtain unauthorized access to member accounts. These attempts are being conducted through text messages and/or phone calls which are made to appear from Kemba Credit Union. With today’s technology, any phone number can be masked as another number to mimic local area codes. In these cases, the fraudsters are masking their real number with Kemba Credit Union’s 513.762.5070.
Below are examples of texts that have been received:
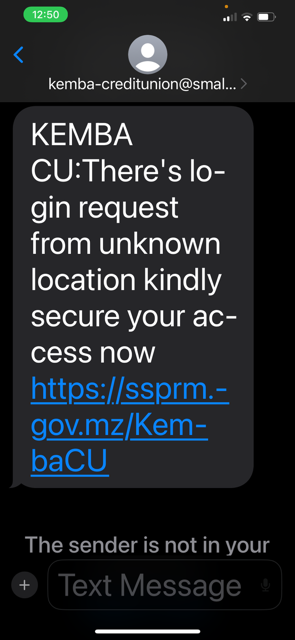
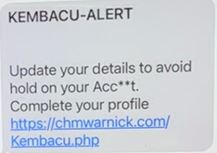

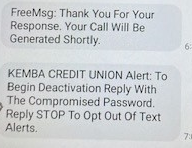
When a member responds with any response to the text, they receive a reply thanking them for their response and a third text is sent asking for their compromised password.
Below is an example of the second and third messages:
Phishing Tips
Phishing attacks use email or malicious websites (clicking on a link) to collect personal and financial information or infect your machine with malware and viruses.
Protect Yourself with these STOP. THINK. CONNECT. tips:
- When in doubt, throw it out: Links in email, tweets, posts, and online advertising are often how cybercriminals try to compromise your information. If it looks suspicious, even if you know the source, it’s best to delete or, if appropriate, mark it as junk.
- Think before you act: Be wary of communications that implores you to act immediately, offers something that sounds too good to be true or asks for personal information.
- Make your password a sentence: A strong password is a sentence that is at least 12 characters long. Focus on positive sentences or phrases that you like to think about and are easy to remember (for example, “I love country music.”). On many sites, you can even use spaces!
- Unique account, unique password: Having separate passwords for every account helps to thwart cybercriminals. At a minimum, separate your work and personal accounts and make sure that your critical accounts have the strongest passwords.
- Lock down your login: Fortify your online accounts by enabling the strongest authentication tools available, such as biometrics, security keys, or a unique one-time code through an app on your mobile device. Your usernames and passwords are not enough to protect key accounts like email, banking, and social media.
How Do You Avoid Being a Victim?
- Don’t reveal personal or financial information in an email, and do not respond to email solicitations for this information. This includes following links sent in email.
- Before sending sensitive information over the Internet, check the security of the website.
- Pay attention to the website's URL. Malicious websites may look identical to a legitimate site, but the URL may use a variation in spelling or a different domain (e.g., .com versus .net).
- If you are unsure whether an email request is legitimate, try to verify it by contacting the company directly. Contact the company using information provided on an account statement, not information provided in an email.
- Keep a clean machine. Having the latest operating system, software, web browsers, anti-virus protection, and apps are the best defenses against viruses, malware, and other online threats.
Scams And Financial Fraud
Telephone Scams
Every year, thousands of people lose their money and personal information to telephone scams. Typically, phone scammers will try to sell you something you hadn't planned to buy and will pressure you to give up personal information, like your credit card details or Social Security number.
Common Phone Scams
In telemarketing fraud, phone scammers will often use exaggerated—or even fake—prizes, products, and services as bait. Some may call you, but others will use mail, text, or ads to get you to call them for more details. Types of phone scams include:
- Travel packages - "Free" or "low-cost" vacations can end up costing a fortune in hidden costs.
- Credit and loans - Popular schemes include advance fee loans, payday loans, and credit card loss protection.
- Fake business and investment opportunities - As business and investing can be complicated, scammers take advantage of people not researching the investment.
- Charitable causes - Many phone scams involve urgent requests for recent disaster relief efforts or emergencies.
National Do Not Call List
Avoid phone scams by registering your home and cell phone numbers with the National Do Not Call Registry or by calling 1-888-382-1222. This national registry was created to offer consumers a choice regarding telemarketing calls. Most legitimate companies don't call if your number is on the registry. If a company is ignoring the registry, there’s a good chance that it’s a scam. If you get these calls, hang up.
Report Telephone Fraud
If you believe you have been a victim of a telephone scam or telemarketing fraud, you can file an online complaint with the Federal Trade Commission (FTC), or by phone at 1-877-382-4357.
Financial Fraud
Scam artists use different types of fraud to try to trick people out of their money. Two common types of fraud are banking scams and investment scams.
Banking Scams
Popular banking scams include:
- Fake check scams: scammers create counterfeit checks that look legitimate, with watermarks, routing numbers, and the names of real financial institutions. They use them to deposit into banks, commit fraud, or pay companies for products or services.
- Unsolicited check fraud: scammers send a check you have no legitimate reason to receive. Unfortunately, if you cash it, you may be authorizing the purchase of items you didn't ask for, signing up for a loan, or something you did not agree to. The Federal Trade Commission offers tips to help you avoid being a victim of these scams, and recommends what to do if you have been a victim.
- Automatic withdrawals: A company sets up unauthorized automatic withdrawals from your account.
- Phishing: Email messages asking you to verify your bank account number or debit card PIN. By clicking on the link or replying to the email with your account number, you are giving a scammer access to your financial accounts.
Investment Scams
Investment scams prey on your desire to earn interest or returns on investments. The Securities and Exchange Commission (SEC) offers overviews of many common investment frauds, and tips to avoid being a victim.
If you are the victim of an investment fraud, you can file a complaint with the SEC or with your state's securities administrator.
For more information and how to report Scams and Financial Fraud you can visit usa.gov.
Family and Friend Imposter Scams
Older consumers are increasingly targeted by scammers pretending to be a loved one in trouble often resulting in large losses.
In the second Consumer Protection Data Spotlight, the Federal Trade Commission examined complaints about family and friend imposter scams, in trouble often claiming to be a grandchild. The FTC is seeing an increase in the number of people ages 70 and over who say they sent cash in response to this particular scam. One in four said they mailed cash in 2018, compared to one in fourteen the prior year. In about half of these cases, the scammer said they were in jail or some other legal trouble and in need of money.
Losses have risen across all age groups, totaling $41 million, compared to $26 million the previous year. The most striking concern is individual losses by older Americans. The median loss for this scam was $2,000, but when seniors 70 and over who mailed cash reported median losses of $9,000.
The FTC urges those who might receive such a call to not act right away. Instead, the FTC recommends calling the family member or friend using a known number, or confirm the request with someone else in their family or a mutual friend.
For more information and how to file a complaint please visit ftc.gov or call the Federal Trade Commission at 877-382-4357.
Tax Related Identity Theft And Remote Takeovers
Protect Yourself from Tax Related Identity Theft
1. Taxes. Security. Together. The IRS, the states and the tax industry need everyone’s help. The IRS launched The Taxes. Security. Together. awareness campaign in 2015 to inform people about ways to protect their personal, tax and financial data. Learn more at www.IRS.gov/TaxesSecurityTogether.
2. Protect Personal and Financial Records. Taxpayers should not carry their Social Security card in their wallet or purse. They should only provide their Social Security number if it’s necessary. Protect personal information at home, and protect personal computers with anti-spam and anti-virus software. Routinely change passwords for online accounts.
3. Don’t Fall for Scams. Criminals often impersonate banks, credit card companies, and even the IRS hoping to steal personal data. Learn to recognize and avoid fake communications. The IRS will not call a taxpayer threatening a lawsuit, arrest, or demanding immediate payment. Beware of threatening phone calls from someone claiming to be from the IRS.
4. Report Tax-Related ID Theft. Here is what taxpayers should do if they cannot e-file their return because someone already filed using their SSN:
- File a tax return by paper and pay any taxes owed.
- File an IRS Form 14039, Identity Theft Affidavit. Print the form and mail or fax it according to the instructions. Include it with the paper tax return and attach a police report describing the theft if available.
- File a report with the Federal Trade Commission using the FTC Complaint Assistant.
- Contact Social Security Administration at www.ssa.gov and type in “identity theft” in the search box.
- Contact financial institutions to report the alleged identity theft.
- Contact one of the three credit bureaus so they can place a fraud alert or credit freeze on the affected account.
- Check with the applicable state tax agency for any additional steps to take at the state level.
5. IRS Letters. If the IRS identifies a suspicious tax return filed using a taxpayer’s stolen SSN, that taxpayer may receive a letter asking them verify their identity by calling a special number or visiting an IRS Taxpayer Assistance Center.
6. IP PIN. If a taxpayer is a confirmed ID theft victim, the IRS may issue an IP PIN. The IP PIN is a unique six-digit number used to e-file their tax return. Each year, they will receive an IRS letter with a new IP PIN.
7. Report Suspicious Activity. If taxpayers suspect or know of an individual or business that is committing tax fraud, they can visit IRS.gov and follow the chart on How to Report Suspected Tax Fraud Activity.
8. Service Options. Information about tax-related identity theft is available online. IRS.gov has a section devoted to identity theft and information for victims to obtain assistance.
For more information on how to protect yourself from tax related identity theft you can visit irs.gov.
How to Prevent Remote Access Takeover Attacks
The IRS urges tax professionals to take the following steps to help protect themselves from remote takeovers:
- Educate staff members about the dangers of phishing scams, which can be in the form of emails, texts, and calls, as well as the threat posed by remote access attacks.
- Use strong security software, set it to update automatically, and run a periodic security “deep scan” to search for viruses and malware.
- Identify and assess wireless devices connected to the network, including mobile phones, computers, printers, fax machines, routers, modems, and televisions. Replace factory password settings with strong passwords.
- Strengthen passwords for devices and software access. Passwords should be a minimum of eight digits (more is better) with a mix of numbers, letters, and special characters.
- Be alert for phishing scams. Do not click links or open attachments from unknown, unsolicited, or suspicious senders.
- Review any software that employees or IT use to support vendors to remotely access the network. Remote access software is a potential target for bad actors to gain entry and take control of a machine. Disable remote access software until it is needed.
For more information you can visit irs.gov.
Elder Abuse Resources
To educate yourself as well as others about awareness surrounding elder abuse visit AARP's BankSafe Insights here. This website contains insight and promising practices on fighting elder exploitation and more.
{endAccordion}

